Recap
Part 2 of this series touched on planning & measuring success of a Cyber Deception campaign. It also covered some "estimations" of Threat Actors based on Operational Security abilities. This part will illustrate more examples of simulation vs dissimulation, for two types of strategic goals: luring & early deterrence/diversion.
How do they get in?
First thing first, how do they get in to start the story we designed for them?
Definition of Attack Surface:
The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment. - US National Institute of Standards & Technology
These entry-points set the stage for the story & contain clues to lead them on or turn them away depending on your goals.
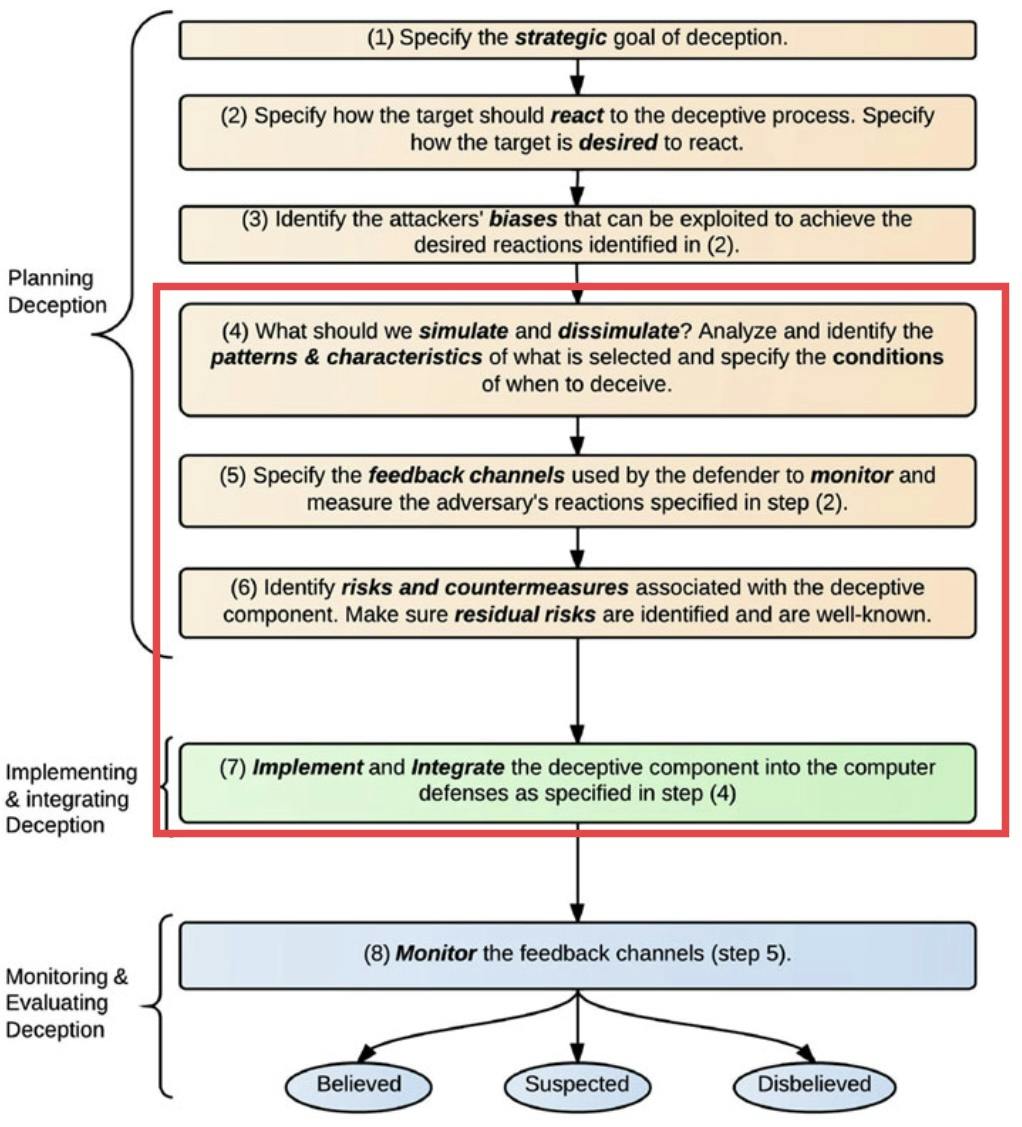
When to simulate or dissimulate?
Part 1 briefly mentioned that deception is all about hiding the real (dissimulation) and showing the false (simulation). So which step is useful for which type of goals?
Fake Malware Analysis SandBoxes
The supreme art of war is to subdue the enemy without fighting.
Positive Technologies did a comprehensive survey of how malware "anti-analysis" techniques have grown over the years. To study how malware operates, sandboxes aim to be “transparent” for the sake of analysis because there is a growing trend of malware authors adding detection logic to abort within a sandbox.
Conversely, if we don't want malware to run (deterrence), then our endpoints should "pretend" (simulate as per
Step 4ofFigure 1) to be Malware Analysis Sandboxes, but without affecting operations, constant updates & invisible to internal users!
All Industrial networks will have some kind of IT network for administrative work & may also need Internet for external communications. Another scenario could be like oil-rigs that are in the middle of an ocean. There are often jump points that have Satellite Internet for external vendors to work within the networks for such cases. All these are examples of infiltration points, some within the Industrial networks & others are from 3rd party remote connections.
There’s a good chance of disrupting custom malware when we implement artifacts that anti-analysis malware are looking for.
The malware did execute, but only to the point it "thinks" that it is in an analysis sandbox!
Feedback Monitoring
We need to know that the fake sandbox deterrence worked, but how? Instead of depending on signature-based detection like COTS Anti-Virus or even "Next-Gen" Endpoint Protection products , which often require Internet link to update databases, we are monitoring access to decoys within endpoints & simulated network ports/services, very often in "air-gapped" operational environments.
Without constant updates, most COTS products are unlikely to detect tailored malware & evasive offensive techniques (e.g. Living-off-the-Land Code Execution). Which is why I worked on offline threat analytics & implemented in OpenEDR for Step 5.
Unlike enterprise endpoints, Industrial endpoints run a much smaller set of programs & usually without Internet. OpenEDR profiles such terminals without Internet & can spot outliers accurately with very low false-positive rates. It is open-sourced, thus allowing further customizations for your unique Deception Campaigns.
Most malware & offensive (e.g. "File-less") code execution will at some point connect to the Internet to get more payloads & also install persistence on the endpoints. We know that fake sandbox simulation worked if there are no further network &/or backdoor installation activities.
What if the malware continues to execute & provides a Command-&-Control (C2) session for the undeterred remote attackers?
More Than Meets the Eye...
Dummy Tanks were used during World War II by both sides, but they did not transform into robots though. During Operation Fortitude, they were used to confuse German intelligence in two ways: first, by making it seem that the Allies had more tanks than they did; and second, to hide and downplay the importance of the location of their real tanks in order to make it seem that the invasion would occur at the Pas-de-Calais rather than at Normandy.
Unless the enemies had gotten hold of the blueprint of your network before the infiltration, they will have to gather information (reconnaissance) once they get a foot-hold into your networks.
Suppose there are 100 assets valuable to attackers, a Deception Defense solution may mimic 100x more of such assets, making it 1% chance (100 real assets / 10,000 total “assets”) of hitting an actual target.
That is the basic working principal behind many COTS Distributed Deception that are operating along side within production networks. Access to diversity & volume of decoys gives us Early Warning Signals. First touch-points could be endpoints & subsequently on the networks (e.g. network queries or scanning to find next targets). For Industrial networks, we need to consider risks (Step 6 of Figure 1) of operational safety, disruptions & other unintended consequences of spoofing certain assets.
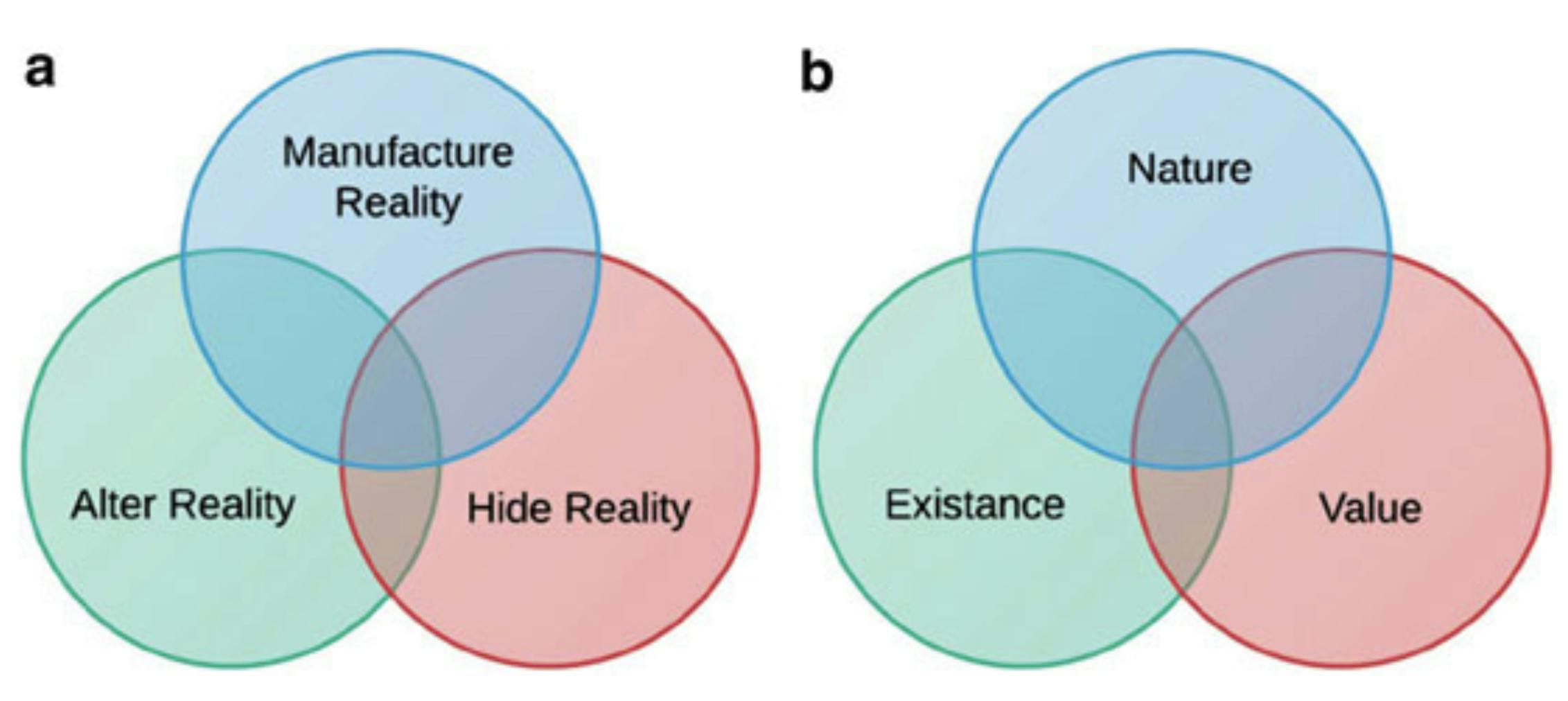
We create deception by (a) manipulating reality (e.g. spoofing more assets, system responses upon query...) & (b) applying to the nature, existence &/or value of data (e.g. implanting malware sandbox artifacts, fake credit-card numbers, user cached credentials or network plans...).
Modern Deception Defense products are turnkey & simplify deployment of such manipulations. These COTS deception solutions are effective against novice & intermediate actors (see Part 2 - Estimation of Threat Actors section) as counter-measures to prevailing Tactics, Techniques & Procedures.

Cyber criminals will eventually catch up with COTS Deception products. Consider HoneyBuster, a free script designed to spot decoys used by common Distributed Deception vendors. Ironically, a product vendor released such a script, which I cloned for posterity.
Try to imagine what stated-sponsored advanced threat actors can do. They get into supply chains like the Solarwind incident & Open-Source projects . They infiltrate Managed Security Service Providers as pivots into their customers & control implants with side-channels that you aren't monitoring , collusion with Insiders & other "Unknown Unknowns".
For the last part of this series , I will share an architectural approach that incorporates a hybrid (COTS + custom decoys) deception defenses, to deal with intermediate to advanced Threat Actors. Please stay tuned!
